In the subject Technology, the topic Basic Computer Science, Networking and Types helps us understand how computers connect and communicate with each other. Networking plays a vital role in sharing data, resources, and information efficiently. This introduction forms the foundation for exploring different types of networks like LAN, WAN, and more.
Previous Year Questions
| Year | Question | Marks |
| 2023 | Write any two differences between IP Address and MAC address. | 2M |
Basic Computer Science
What is a Computer System?
A computer system is a programmable digital electronic device. It accepts input in the form of data, processes this data based on program instructions, and outputs information in a desired format for meaningful use.
The interaction between the user and the system happens through application software:
- The user provides input data.
- Application software processes the data with the help of the operating system.
- The processed data (program output) is delivered to an output device like a monitor, printer, or storage device.
The CPU (Central Processing Unit), also known as the microprocessor, executes the instructions provided by the application software to process the input and generate the desired output.
Features of a Computer System
Programmable
- A computer system performs tasks only according to program instructions.
- The accuracy of the output depends on the accuracy of the input and the instructions. If the input or instructions are incorrect, the result will also be inaccurate—this is often summarized as Garbage In, Garbage Out (GIGO).
Processes Raw Data into Information
- Computers transform unprocessed, raw data into meaningful information by executing program instructions.
Digital Machine
- Computers operate in binary code, consisting of 0s and 1s. They are known as machine code or machine language.
- Programs written in human-readable high-level languages (e.g., C++, Python, Java) are translated into machine code for the computer to execute. This translation process is called program compilation.
- The CPU decodes and executes machine instructions. Each instruction performs a specific task as part of the overall program.
A computer system consists of two major components:
hardware and software.Hardware includes the physical components of the computer, some of which are housed inside the computer case, while others are connected externally.
- Motherboard: The main circuit board connecting all hardware components.
- Hard Disk Drive (HDD): Provides non-volatile storage for data and programs.
- Power Unit: Supplies electrical power to the system.
- Central Processing Unit (CPU): The “brain” of the computer responsible for executing instructions and performing arithmetic and logical operations.
- Random Access Memory (RAM): Temporary, volatile memory used for processing data and instructions.
- Cooling Fans: Maintain optimal temperatures to prevent overheating.
- Computer Buses: Facilitate communication between components.
Software refers to the programs that direct the hardware to perform user-specified operations.
- Software refers to programs—sets of instructions directing the hardware to perform specific tasks.
- Programs are written in high-level programming languages and must be converted into low-level binary machine code for execution.
- Examples of programming languages include C, C++, Java, and Python.
Components of a Computer System
A computer system comprises four basic components or functional units. These components are:
- Input Devices (Input Unit)
- Central Processing Unit (CPU)
- System Memory (Memory Unit)
- Output Devices (Output Unit)
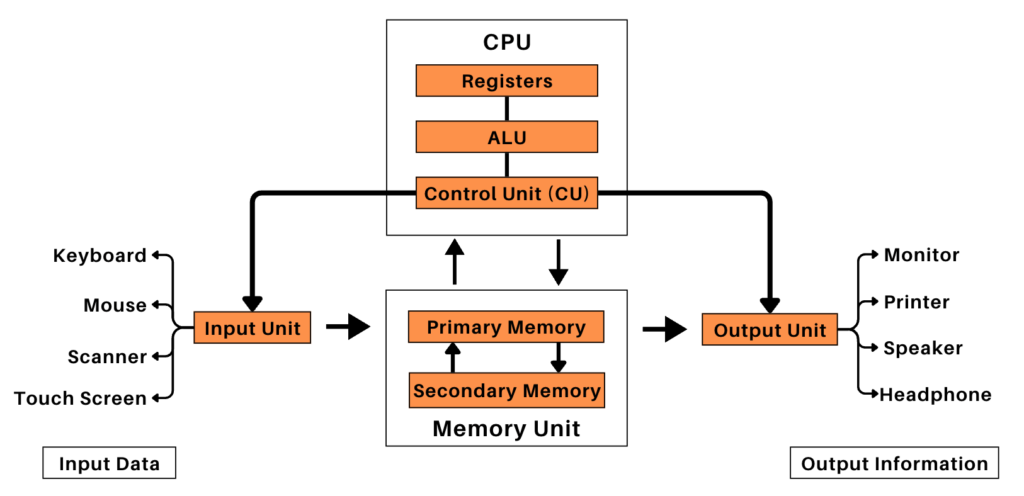
Input Unit
- Purpose: Send user data/commands to the computer in a digital format.
- Examples:
→ Keyboard, mouse, scanner, touch screen.
→ Voice input (e.g., Google Voice Search).
→ Braille keyboard (for visually impaired). - The input data is transferred to the CPU for processing based on the instructions provided by the program.
- Data Storage: Temporarily stored in RAM; saved in secondary memory for long-term use.
Output Unit
- Purpose: Convert processed data into human-understandable forms.
- Examples:
→ Visual: Monitor, projector.
→ Audio: Speaker, headphones.
→ Hardcopy: Printer (inkjet, laser, dot matrix, 3D).
→ Braille display monitor (for visually impaired). - 3D Printers: Create physical replicas of digital designs; used in industries and medicine. (Additive manufacturing)
Memory Unit
The memory unit is a crucial part of the computer system, responsible for storing program instructions and data before, during, and after processing. It consists of:
- Temporary Memory (Primary Memory):
- Random Access Memory (RAM):
- Stores data and instructions required during program execution.
- Volatile: Loses all data once the power is switched off.
- Enables fast access for immediate processing.
- Random Access Memory (RAM):
- Permanent Memory (Secondary Memory):
- Hard Disk Drive (HDD), Solid-State Drive (SSD), Pen Drives, etc.
- Non-volatile: Retains data even when the power is off.
- Used for long-term storage of data and programs.
- Hard Disk Drive (HDD), Solid-State Drive (SSD), Pen Drives, etc.
The memory hierarchy organizes these memory types based on their speed, size, cost, and proximity to the CPU, optimizing performance.
Central Processing Unit (CPU)
- The CPU (Central Processing Unit) is the “brain” of a computer. Just like your brain controls all the activities in your body, the CPU controls all the tasks a computer performs.
- The CPU works in tandem with the memory and input/output units to ensure smooth operation of the system.
Functions of the CPU:
- The CPU retrieves program instructions and data from the memory.
- It performs all arithmetic and logical operations specified in the instructions.
- The processed results are stored back in the memory.
CPU Components:
- Registers:
- Local memory within the CPU for temporarily storing data, instructions, and intermediate results.
- Registers are limited in size and number but are critical for high-speed operations.
- Arithmetic Logic Unit (ALU):
- Executes all arithmetic and logical operations required by the program.
- Control Unit (CU):
- Oversees sequential instruction execution.
- Interprets instructions and manages data flow between memory, the ALU, and input/output devices.
Evolution of Computers
Early Mechanical Computers
- Abacus (500 BC): The first known tool for basic arithmetic operations like addition and subtraction.
- Pascaline (1642): Blaise Pascal invented a mechanical calculator capable of performing addition, subtraction, multiplication, and division through repeated operations.
- Analytical Engine (1837): Charles Babbage designed the first mechanical computing device with input, processing, storage, and output capabilities. It introduced the concept of programmability.
- Tabulating Machine (1890): Herman Hollerith created a machine using punched cards to summarize data, marking the start of data processing and early programmable systems.
- Turing Machine (1937): Alan Turing conceptualized a programmable machine capable of executing instructions stored on punched cards, forming the foundation of modern computer algorithms.
First Generation (1940–1956): Vacuum Tube Computers
- Technology: Used vacuum tubes for processing and memory, machine language for programming, and magnetic drums for storage.
- The Von Neumann architecture laid the foundation for modern computing.
- Key Features:
- Large size, high power consumption, and limited memory (measured in kilobytes).
- Operated with punched cards and paper tape for input and printouts for output.
- Examples:
- The Electronic Numerical Integrator and Computer (ENIAC – 1946) was the first binary programmable computer based on the Von Neumann architecture; EDVAC (Electronic Discrete Variable Automatic Computer)
- UNIVAC I (1951): The first commercially available computer.
- Limitations:
Slow, unreliable, and required significant maintenance.
Second Generation (1956–1963): Transistor Computers
- Technology: Transistors replaced vacuum tubes, making computers smaller, faster, and more reliable.
- Programming: Transitioned from machine language to assembly language and introduced high-level languages like FORTRAN and COBOL.
- Memory: Used magnetic cores and disk storage, with memory increasing to megabytes (MB).
- Key Features:
- Lower power consumption and increased efficiency.
- Businesses started adopting computers for commercial purposes.
- Examples: IBM 1401 and Programma 101 (one of the first desktop computers).
Third Generation (1964–1971): Integrated Circuit (IC) Computers
- Technology: Introduced Integrated Circuits (ICs), which combined multiple transistors into a single silicon chip.
- Operating Systems: Developed to manage hardware and software, enabling multitasking.
- Memory: Introduced RAM and semiconductor memory, increasing capacity to several megabytes (MB).
- Key Features:
- Smaller, more affordable, and reliable computers.
- Advanced programming languages and increased data-handling capabilities.
- Examples: IBM System/360 series.
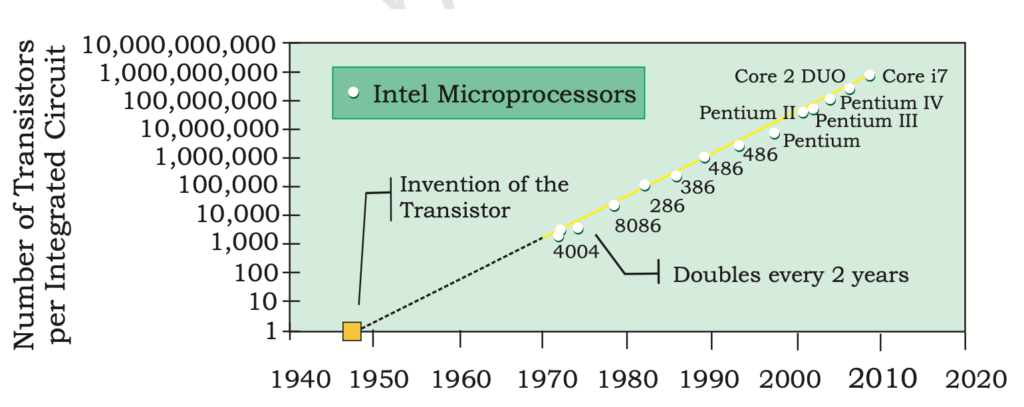
Fourth Generation (1971–Present): Microprocessor Computers
- Technology: Microprocessors (e.g., Intel 4004 in 1971)
- 1970s: → During the 1970s, Large Scale Integration (LSI) enabled the integration of a complete CPU onto a single chip, giving birth to the microprocessor.
- Moore’s Law: Predicted exponential growth in transistor density on chips.
- 1980s: → Very Large Scale Integration (VLSI): Around 3 million components integrated on a small chip.
- Later: → Super Large Scale Integration (SLSI): ~10⁶ components on a single IC.
- 1970s: → During the 1970s, Large Scale Integration (LSI) enabled the integration of a complete CPU onto a single chip, giving birth to the microprocessor.
- Memory:
Transitioned to DRAM and SSD storage, with memory capacities expanding to gigabytes (GB) and terabytes (TB). - Key Features:
- Rise of personal computers (PCs) with user-friendly Graphical User Interfaces (GUIs).
- Examples: IBM PC (1981) and Apple Macintosh (1984).
- 1980s-1990s: →The shift from command-line interfaces (CLI), like UNIX and DOS, to GUI-based operating systems (e.g., Microsoft Windows) made computers more intuitive and user-friendly.
- World Wide Web (1991): Introduced by Tim Berners-Lee, making the internet widely accessible.
- Mobile Computing (2000s): Rise of smartphones and tablets revolutionized computing.
The Future of Computers
- AI Integration: AI-based systems with self-learning, natural language processing, and robotics. Examples: IBM Watson and autonomous vehicles.
- Quantum Computing:
- Explores the use of quantum mechanics for unparalleled processing speeds.
- Google’s Quantum Supremacy (2019): Demonstrated a quantum computer solving problems in seconds that would take traditional supercomputers millennia.
- Biological and DNA Computers:
Mimic biological systems for advanced data processing. - Brain-Computer Interfaces (BCIs):
Aim to directly link the human brain with computers, enabling seamless interaction - Edge Computing: Bringing computation closer to data sources for real-time processing.
A punched card is a piece of stiff paper that stores digital data in the form of holes at predefined positions.
Moore’s Law: In 1965, Intel co- founder Gordon Moore introduced Moore’s Law which predicted that the number of transistors on a chip would double every two years while the costs would be halved.
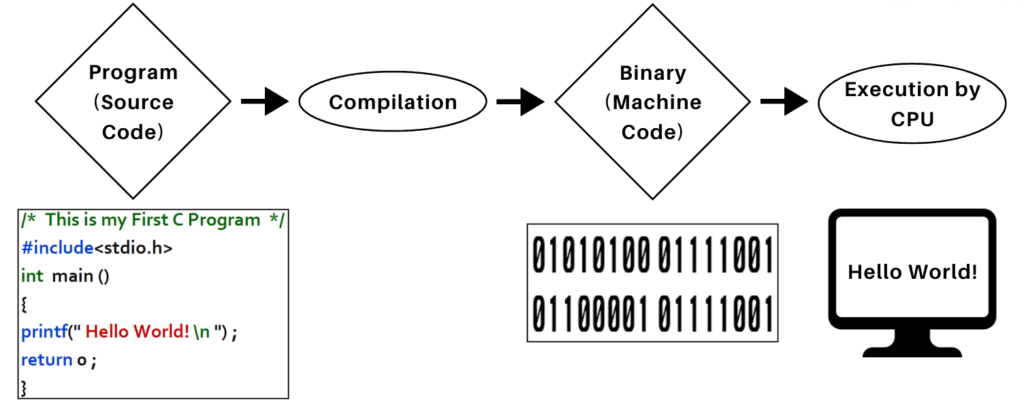
Computer Program:
- A computer program is a sequence of instructions written to perform a specific task on a computer.
- After writing a program, it can be saved as an executable file (.exe) to perform the intended task.
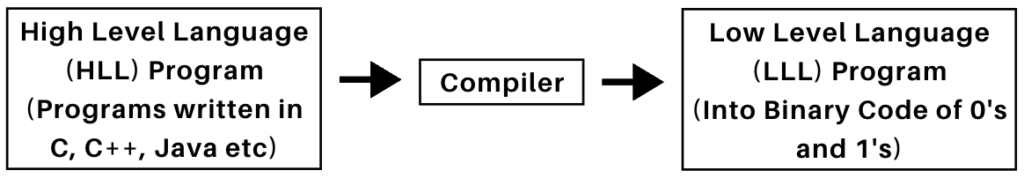
Why Do Computer Programs Need to Be Converted to Binary?
Computer programs are typically written in high-level programming languages like C, C++, Java, or Python, which are easier for humans to read and understand. However, computers are digital electronic devices that can only interpret and execute instructions in binary machine code.
Conversion Process:
- High-Level Code: Programs written in human-readable languages.
- Compiler: A specialized software translates the high-level program into binary (machine code).
- Machine Code: The CPU executes the binary instructions to perform operations.
What Is the Binary Number System?
The binary number system is a base-2 numeral system that uses only two digits: 0 and 1. It is extensively used in digital electronics because of its straightforward implementation. In digital systems:
- 1 represents the ON state.
- 0 represents the OFF state
Number Systems
| Number System | Base | Digits | Usage |
| Binary | 2 | 0, 1 | Fundamental for computer systems |
| Decimal | 10 | 0, 1, 2, …, 9 | Commonly used by humans |
| Octal | 8 | 0, 1, 2, …, 7 | Compact representation of binary |
| Hexadecimal | 16 | 0, 1, 2, …, 9, A-F | Memory addressing, color codes |
Networking and Types
What Are Computer Networks?
A computer network is a system where two or more computers/devices are connected to exchange information, share resources (like printers or files), and communicate effectively.
Key Components of Computer Networks:
- Nodes (Devices): A device within the network that can send, receive, or store data.
- Computers, smartphones, printers, or servers connected to the network.
- Data Communication: Information is divided into smaller chunks called packets, which are transmitted over the network.
- Communication Links: The “roads” data travels on.
- Wired: Using cables like Ethernet.
- Wireless: Using mediums like air (Wi-Fi, Bluetooth).
- Protocols: Rules ensuring devices “speak the same language” (like TCP/IP, HTTP).
Types of Computer Networks
Computer networks vary in size, range, and purpose. They can range from personal devices connected via Bluetooth within a single room to global networks interconnecting millions of devices. Networks are classified based on their geographical area and data transfer rates into four broad categories:
- Personal Area Network (PAN)
- Local Area Network (LAN)
- Metropolitan Area Network (MAN)
- Wide Area Network (WAN)
| Characteristic | Personal Area Network (PAN) | Local Area Network (LAN) | Metropolitan Area Network (MAN) | Wide Area Network (WAN) |
| Definition | A network that connects personal devices within a small range (~10 meters). | A network that connects devices within a limited area such as a building or campus. | A network that connects devices across a city or large campus.Often formed by connecting multiple LANs. | A large network that spans across a broad geographical area, such as countries or continents.Connects multiple LANs and MANs via wired or wireless media. |
| Range | Up to 10 meters (approx. 30 feet) | Up to 1 km (approx. 0.6 miles) | A few kilometers up to 100 km | Hundreds to thousands of kilometers |
| ConnectionMedium | Wired: USB cable, EthernetWireless (WPAN): Bluetooth, Zigbee, NFC, RFID, Infrared, UWB (Ultra-Wideband) | Wired: Ethernet, Fiber Optic Cables (for high-speed LANs)Wireless(WLAN): Wi-Fi (Wireless LAN), WiMAX (less common), Z-Wave | Wired: Fiber optics, leased lines, Wireless: Microwave Links, WiMAX, LTE (Long-Term Evolution) | Wired: Fiber Optic Cables, Leased Lines, Satellite Links, DSL/CableWireless: Satellite Communication, Microwave Links, Cellular Networks (e.g., 4G/5G) |
| Speed | Typically 1 Mbps to 100 Mbps | 100 Mbps to 10 Gbps{Ethernet: ~10 MbpsGigabit Ethernet: ~1000 Mbps} | 10 Mbps to 1 Gbps{Moderate speed, lower than LAN} | 56 Kbps to several Gbps |
| Use Case (Application) | Connecting personal devices like smartphones, tablets, and laptops.Low power consumption, limited to individual or home use. | High-speed connectivity for internal communication and sharing.Office networks, home networks, school networks. | Ideal for interconnecting city-based networks, public Wi-Fi hotspots. | Global communication, Internet, Connecting branch offices. |
| Examples | Bluetooth headset, smartphone-to-laptop connection | Home Wi-Fi, office Ethernet network | City-wide internet access, university campus network | The Internet, corporate WANs connecting regional offices |
Fig: PAN
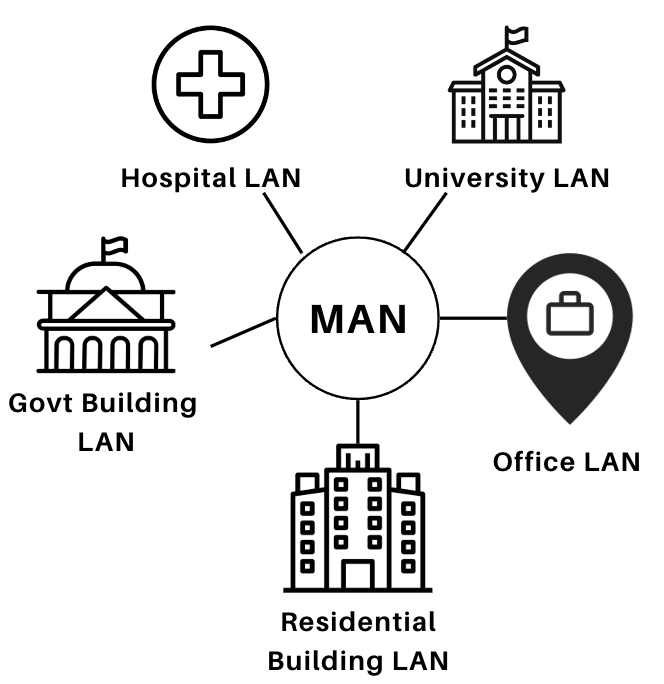
Fig: MAN
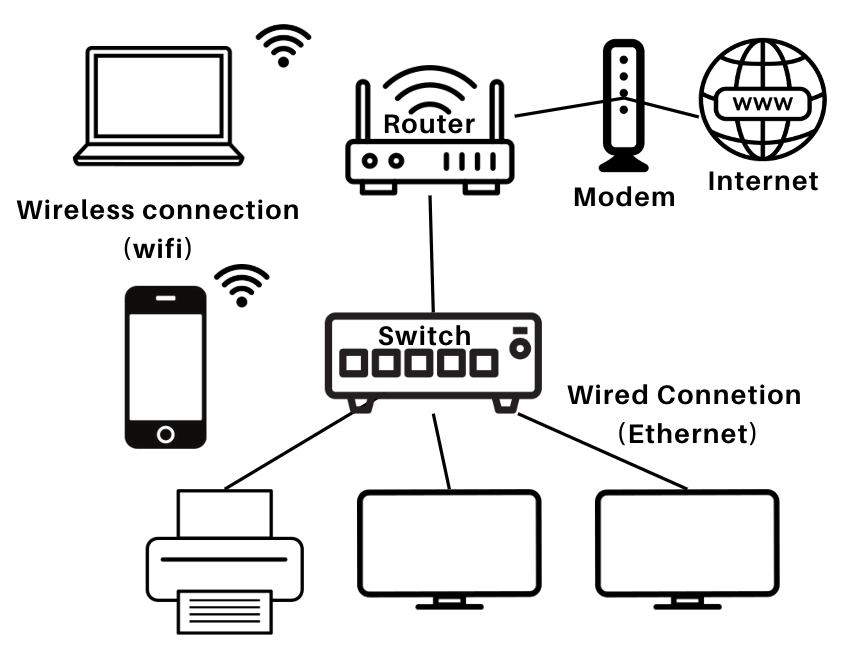
Fig: LAN
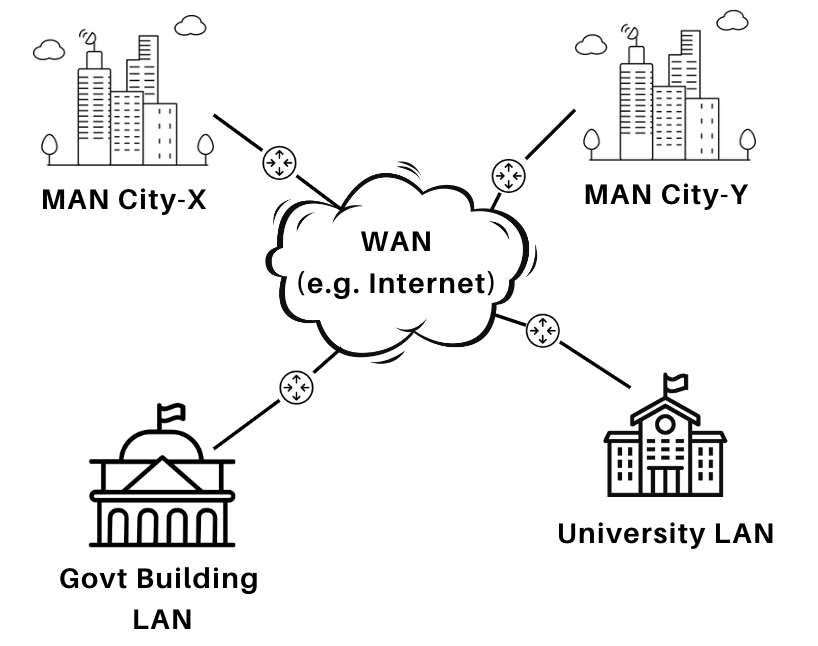
Fig: WAN
VPN (Virtual Private Network)
A Virtual Private Network (VPN) is a service that creates a secure connection over the internet to protect your data and privacy.
- Virtual because no physical cables are involved in the connection process.
- Private because through this connection, no one else can see your data or browsing activity.
- Networked because multiple devices—your computer and the VPN server—work together to maintain an established link.
How Does It Work?
- Encryption: Your data is encrypted (turned into unreadable code) to protect it from hackers.
- Secure Tunnel: VPN creates a “tunnel” for your data to travel securely.
- IP Masking: Your real IP address is hidden, making you appear from a different location.
Why Use a VPN?
- Privacy & Security: Encrypts your data, keeping it safe from hackers, especially on public Wi-Fi.
- Access Restricted Content: Lets you access content that is blocked in your region (e.g., Netflix, websites).
- Bypass Censorship: Allows access to websites blocked by governments or organizations.
- Avoid Tracking: Hides your IP address to prevent tracking by websites or advertisers.
- Secure Remote Access: Allows employees to securely connect to company networks when working remotely.
Drawbacks of VPN
- Slower Speeds: Encryption can slow down internet speeds.
- Dependable VPN Providers: Some providers may not offer strong security or privacy.
Network Devices
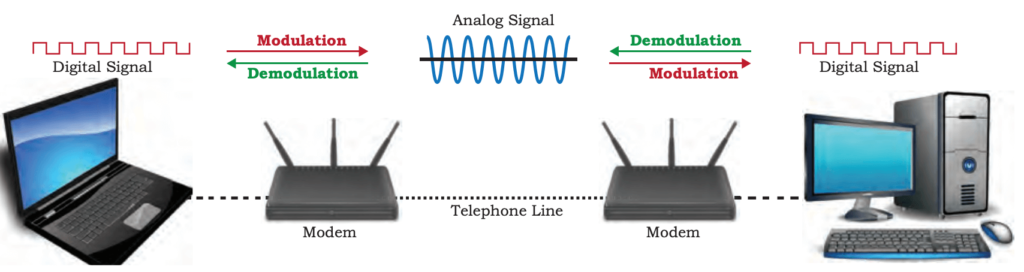
Modem
- Full Form: MOdulator DEModulator
- Function: Converts digital data to analog signals and vice versa.
- At the sender’s end: The modem modulates the digital data into analog signals.
- At the receiver’s end: The modem demodulates the analog signal back into digital data.
Ethernet Card (NIC – Network Interface Card)
- Function: It is a network adaptor that allows computers to connect to a network via a physical cable. It is installed on the motherboard and connects to the network through an Ethernet cable.
- Data Transfer Speed: Typically ranges from 10 Mbps to 1 Gbps.
- MAC Address: Each NIC has a unique address (MAC) that identifies the computer on the network.
- When you connect your computer to a wired local network, it uses the NIC to send and receive data.
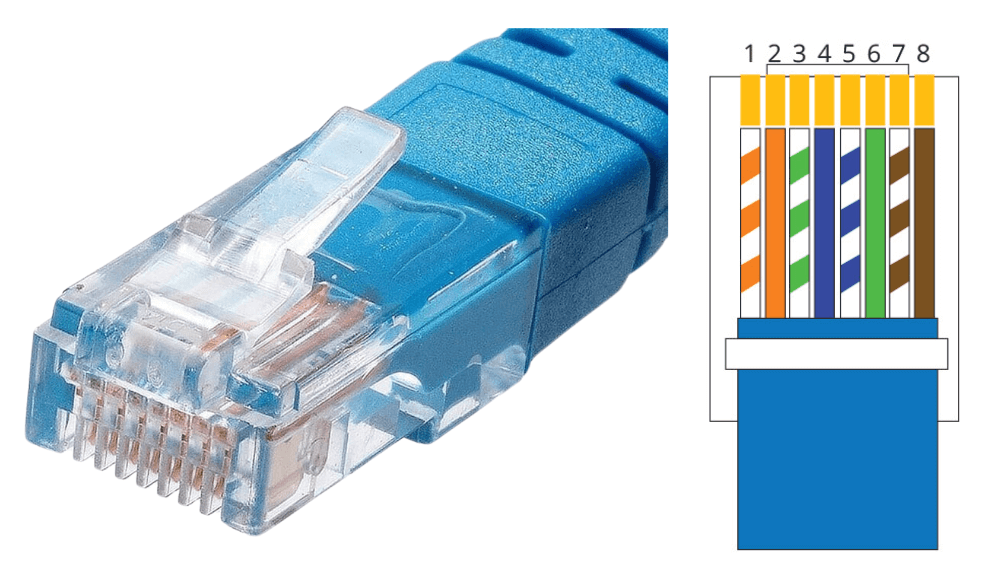
RJ45
- Function: A standard 8-pin connector used with Ethernet cables.
- Purpose: To connect devices like computers and routers to the network using Ethernet cables.
Repeater
- Signal weakens over long distances (typically beyond 100 meters)
- Function: It is an analogue device that regenerates and amplifies signals to extend their travel distance.
Hub
- Function: A basic network device that connects multiple devices in a LAN. It broadcasts data to all connected devices.
- Limitation: It does not distinguish between devices; all data packets are sent to every device, and if two devices send data at the same time, a collision can occur.
- Example: An old-fashioned office network setup with multiple computers and printers all connected via a hub.
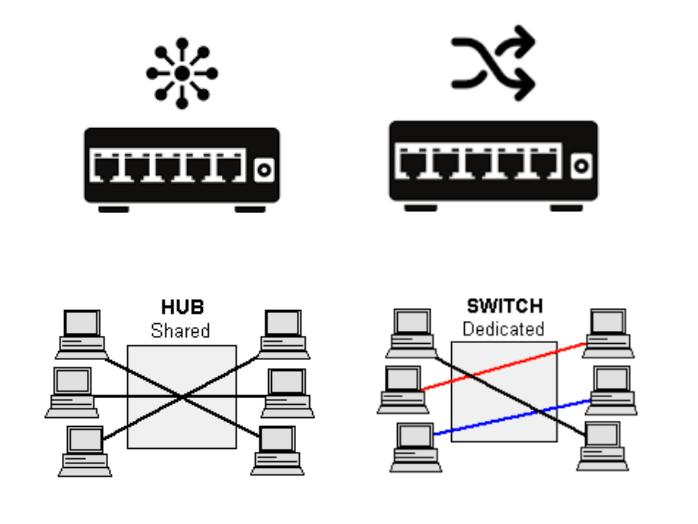
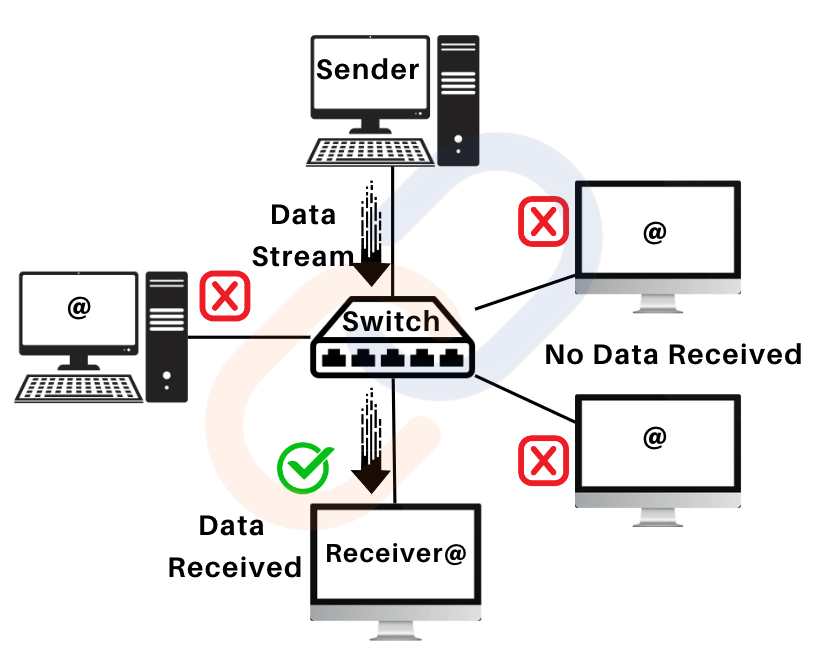
Switch
- Function: More advanced than a hub, a switch connects devices in a LAN and forwards data to the specific device based on the MAC address in the data packet.
- Advantages Over Hub: It can handle multiple transmissions simultaneously, reduces data collision, and drops noisy/corrupted signals.
- Example: A modern office network where computers and printers are connected via a switch for efficient data transfer.
Router
- A router is a networking device that connects different networks (e.g., a Local Area Network (LAN) to the internet).
- Primary Function: It routes data packets between networks using IP addresses and determines the best path for data transmission.
- Typically, a router also functions as a gateway in smaller networks, such as in home or office setups
Key Features:
- Packet Routing: Uses protocols like IP to forward data packets to their destination.
- Inter-network Communication: Connects multiple networks (e.g., a home network to the internet).
- Wireless and Wired Connectivity: Many routers provide Wi-Fi for wireless access and Ethernet ports for wired connections.
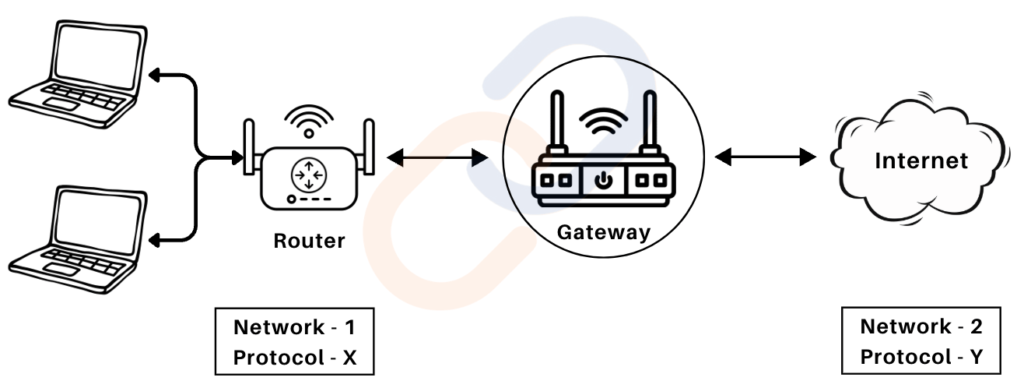
Gateway
- A gateway is a device that acts as an entry and exit point for a network (a “gate”). It connects two networks with different protocols, architectures, or data formats.
- Primary Function: It translates and forwards data between networks, enabling communication between incompatible systems.
- Example: A gateway device in a corporate environment ensures secure data transfer between the company’s internal network and external networks like the internet.
- Key Features:
- Protocol Conversion: Converts data between two networks using different protocols.
- Access Point: Serves as the “gate” where all incoming and outgoing data must pass.
- Firewall Integration: Often includes security features to protect the internal network.
Networking Topologies
Network topology refers to the arrangement of devices (nodes) and connections in a network. Each topology has unique features, advantages, and limitations.
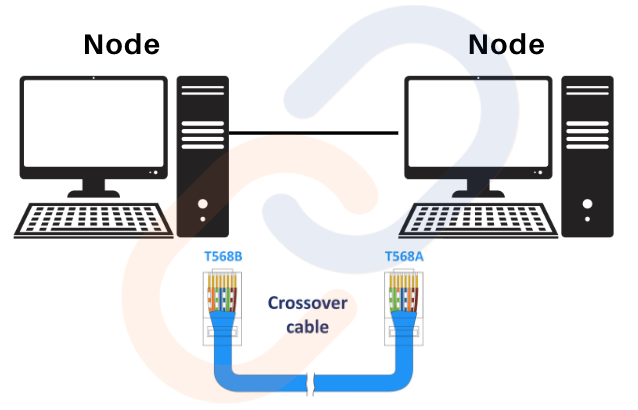
Point-to-Point (P2P) Topology
- Structure: Direct connection between two devices using a single cable.
- Use Case: Connecting two computers directly for file sharing.
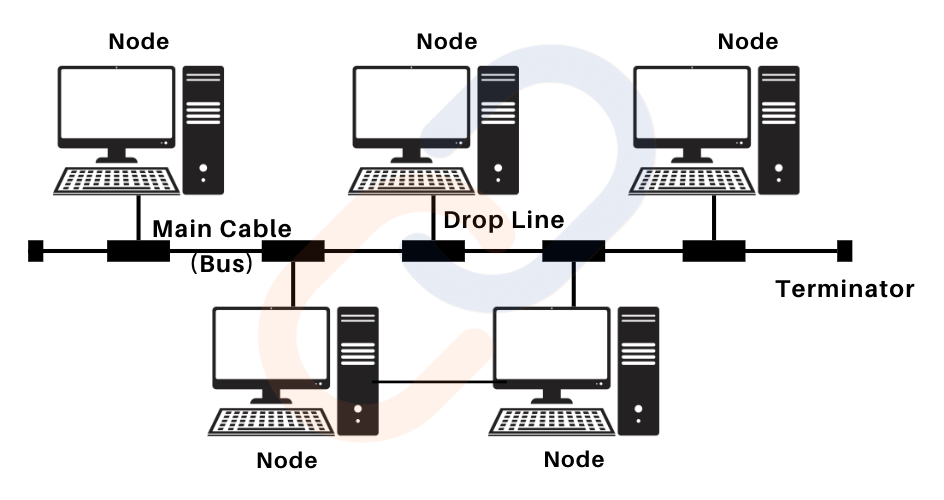
Bus Topology
- Structure: All devices are connected to a single backbone cable (the bus), with drop lines linking individual devices.
- Working Principle
- Half-Duplex Communication:
- Data travels in one direction at a time.
- Broadcast Communication:
- Packets are sent to all devices, but only the target device processes the packet by verifying the destination MAC address.
- Half-Duplex Communication:
- Use Case:
- Ideal for small, cost-sensitive networks with limited devices.
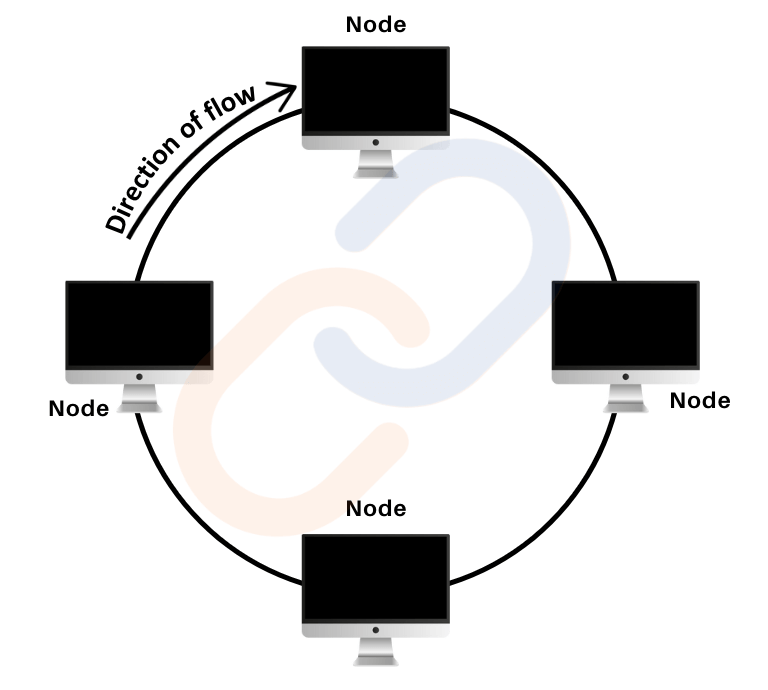
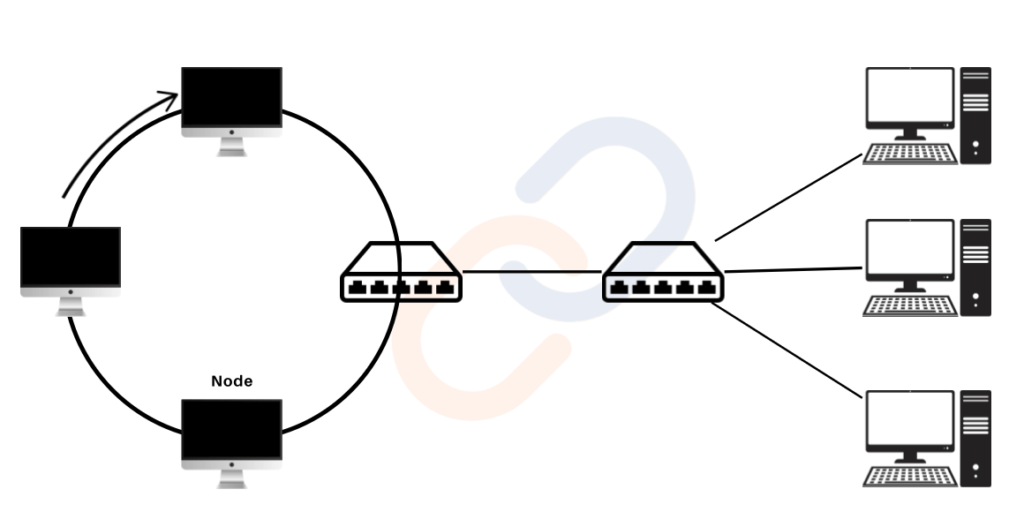
Ring Topology
- Structure: A ring network topology connects each device (station) to two others, forming a circular pathway for data transmission.
- Features:
- Data travels sequentially in one direction (half-duplex mode).
- For large networks, repeaters prevent signal loss by amplifying data signals.
- Working Principles
- Sequential Transmission:
- Data passes through intermediate nodes until reaching the destination.
- Sequential Transmission:
- Use Case: Small office networks or LANs requiring predictable data flow.
- Historically popular in LANs during the 1990s.
- Replaced by star topology due to limitations like low speed (4-16 Mbps).
- Still used in optical fiber rings for ISPs and MSPs in wide-area networks (WANs).
Star Topology
- Star network topology is one of the most widely used configurations in networking due to its simplicity, scalability, and reliability.
- Structure: It uses a central hub or switch as the focal point, with all other network devices connecting to this central unit.
- Working Principle:
- Data packets are sent from a source device to the switch, which forwards them to the intended destination device based on the MAC address.
- Use Case: Common in home and office networks.
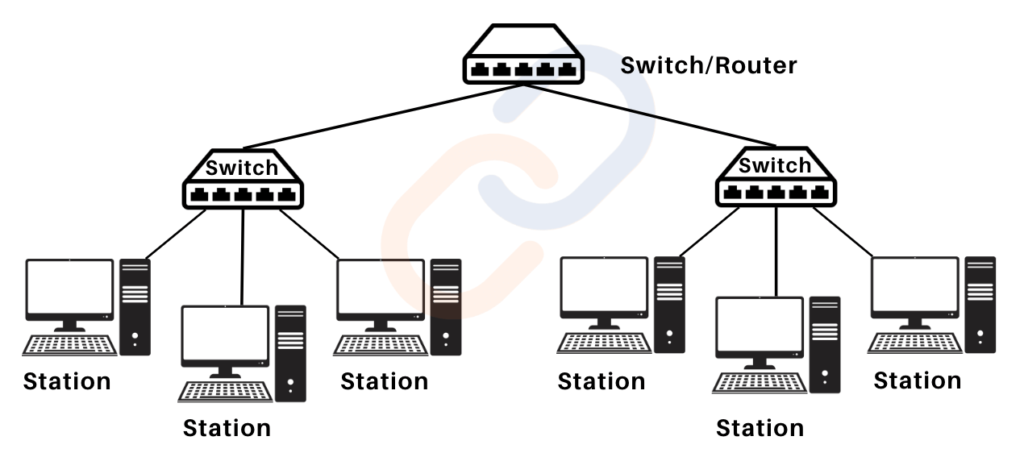
Tree (Hybrid) Topology
- Structure: A hierarchical combination of other topologies, like star, ring, or bus.
- It uses a root switch (or main hub) that connects to branch switches, forming a layered structure resembling a tree.
- Stations (devices) connect to switches, and multiple branches (subnetworks) stem from the main switch.
- Role of Routers: Subnetting and firewall integration
- Use Case: WANs (Wide Area Networks) and large organizations with hierarchical structures.
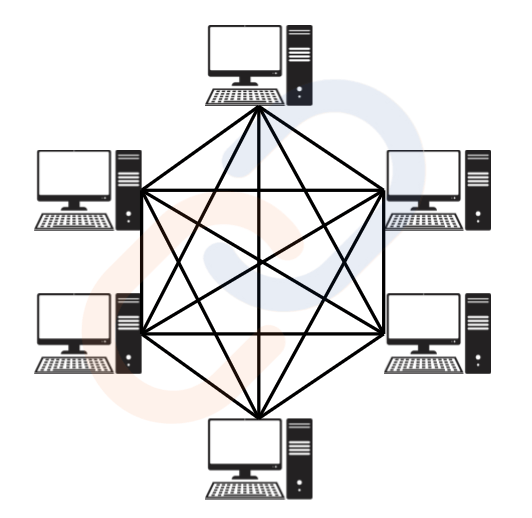
Mesh Topology
- Structure: Every device is directly connected to every other device.
- Features:
- High reliability: Failure of one link doesn’t affect the network.
- High data traffic capacity: Multiple nodes can transmit simultaneously.
- Secure: Each link carries unique data between devices.
- Drawbacks:
- High cabling cost and complexity.
- Many unused or redundant connections.
- Use Case: Military communication systems or critical systems where reliability is paramount.
Hybrid Network Topology
- Structure: A hybrid network topology combines two or more network topologies (e.g., star and ring) to leverage their strengths and adapt to specific needs.
- Features:
- Scalable: Easily accommodates network growth.
- Flexible: Combines the advantages of individual topologies.
- Complex: Inherits both the benefits and drawbacks of its components, making installation and maintenance more challenging and costly.
- Example: Star-Ring Hybrid
- Ring: Modern fiber rings connect distant nodes across cities. If one link fails, reserve channels maintain connectivity.
- Star: Local area networks use the star topology for efficient, short-distance connections.
- Advantages:
- Reliability: Redundant paths prevent single points of failure.
- Adaptability: Fiber media converters enable integration of fiber and copper-based equipment.
- Applications:
- Ideal for large networks requiring long-distance connections and efficient local setups, such as inter-building or inter-city networks.
Identifying Nodes in a Network
Each node (device) in a network requires a unique identifier to enable communication. Two key identifiers used are:
MAC Address (Media Access Control Address)
- A permanent physical address unique to every network interface card (NIC).
- How it’s created: Engraved during manufacturing. It cannot be changed.
- Structure:
- 48-bit hexadecimal number (12 digits).
- Split into two parts:
- First 6 digits (OUI): Manufacturer’s ID.
- Last 6 digits: Serial number of the card.
- Example: 00:1A:2B:3C:4D:5E.
- Use: Physically identifies a device in a network.
- Note: can find a computer’s MAC address by typing ipconfig /all (Windows) or ifconfig (Linux/Mac) in the command prompt or terminal.
IP Address (Internet Protocol Address)
- A logical address for identifying a device in a network.
- Features:
- Dynamic: Can change when the device switches networks.
- Allows communication globally.
Types of IP Addresses:
- IPv4 (Internet Protocol Version 4):
- Length: 32 bits.
- Format: Four decimal numbers separated by periods.
- Range: Each number from 0–255.
- Example: 192.168.0.178.
- Limitations: Can address approximately 4.3 billion devices—insufficient for modern needs.
- IPv6 (Internet Protocol Version 6):
- Length: 128 bits (for a much larger address space).
- Format: Eight hexadecimal groups separated by colons.
- Example: 2001:CDBA:0000:0000:0000:0000:3257:9652.
- Advantage: Provides a virtually unlimited number of addresses to meet growing demand
Key Differences Between MAC and IP Addresses:
| Feature | MAC Address | IP Address |
| Full Form | Media Access Control Address | Internet Protocol Address |
| Purpose | Identifies hardware device | Identifies device in a network |
| Scope | Local network identification (LAN) | Global network identification (WAN/Internet) |
| Length | 48 bits | 32 bits (IPv4) / 128 bits (IPv6) |
| Assigned By | Manufacturer during hardware production | Internet Service Provider (ISP) or DHCP server |
| Permanence | Permanent and unique | Dynamic or static (can be reassigned) |
| Visibility | Seen within the local network | Can be accessed globally |
| Routing Role | Operates at Data Link Layer (Layer 2) | Operates at Network Layer (Layer 3) |
| Format | Hexadecimal (e.g., 00:1A:2B:3C:4D:5E) | IPv4: Decimal (e.g., 192.168.0.178) |
| Tracking | Used for identifying specific hardware | Used for locating a device on the Internet |
| Changeability | Cannot be changed | Can be changed when switching networks |
| Security Use | Used in MAC filtering for network access control | Can be hidden or masked via VPNs and proxies |
Internet, Web, and the Internet of Things (IoT)
The Internet
- Definition: A global network connecting computing devices such as desktops, laptops, servers, tablets, mobile phones, and smart devices (e.g., TVs, refrigerators, drones).
- It’s like the “highway” that carries data between devices, whether it’s emails, websites, or videos.
- Components:
- Devices connect via modems, wired or wirelessly (WiFi).
- Local networks connect to Internet Service Providers (ISPs).
- ISPs form regional, national, and international networks, creating the Internet backbone.
The World Wide Web (WWW)
- The Web (World Wide Web) is a service that runs on the Internet. It’s made up of websites, pages, and content that we access using browsers (like Chrome or Safari).
- History: Invented in 1990 by Sir Tim Berners-Lee, who introduced three key technologies:
- HTML (HyperText Markup Language):
- URI (Uniform Resource Identifier):
- HTTP (HyperText Transfer Protocol):
- How it works: When you type a website address (URL), your browser fetches data from a server using HTTP or HTTPS and displays the content (like text, images, and videos).
Key Difference: Internet vs. WWW
| Aspect | Internet | World Wide Web (WWW) |
| Definition | A global network of interconnected devices. | A collection of interlinked webpages accessible online. |
| Purpose | Facilitates communication and data sharing. | Provides a platform for accessing and sharing information. |
| Examples | Computers, routers, IoT devices. | Websites, blogs, e-commerce platforms. |
What is the Internet of Things (IoT)?
The Internet of Things (IoT) is a system where everyday objects (like fridges, cars, and even light bulbs) are connected to the internet and can communicate with each other and with us.
How Are They Related?
- The Internet is the infrastructure that connects devices and allows data exchange.
- The Web is a service that runs on the internet, providing us with websites and online content.
- IoT uses the internet to connect everyday devices, enabling them to share data and automate tasks without human intervention.
Domain Name System (DNS) and Domain Name Resolution
The Need for Domain Names
- The Internet is made up of millions of websites, each stored on a server connected to the network.
- Every server has a unique IP address, which is a series of numbers that identifies the server. However, remembering IP addresses for each website is difficult.
- Instead of remembering these numeric addresses, we assign human-readable names to each server’s IP address. These names are known as Domain Names or Hostnames.
Example:
- Domain Name: ncert.nic.in
- IP Address: 164.100.60.233
Each website has its domain name (hostname) associated with its IP address.
DNS Query Process:
When you enter www.ncert.nic.in in your browser:
- HTTP Request → Your browser requests the IP address of the domain.
- DNS Query → The browser asks a DNS server for the corresponding IP address.
- DNS Response → The DNS server returns the IP address, e.g., 164.100.60.233.
- HTTP Response → The browser uses the IP address to retrieve the website and display it.
Evolution of the World Wide Web
Web 1.0 (The Static Web)
- Timeframe: 1990s to early 2000s
- Invented by Tim Berners-Lee in 1989 and went live in 1991.
- Nature: Static, read-only
- Example:Simple websites like personal blogs or informational pages.
Web 2.0 (The Social Web)
- Timeframe: Mid 2000s to present.
- The term Web 2.0 was popularized by Tim O’Reilly in 2004, signifying a shift from static, informational sites to dynamic, interactive platforms where users could contribute and collaborate.
- Nature: Interactive, dynamic, user-generated content.
- Example:
- Social media platforms (Facebook, Instagram, Twitter)
- Online marketplaces (e.g., Amazon, eBay)
- Video sharing platforms (e.g., YouTube, Vimeo)
Web 3.0 (The Semantic Web and Decentralized Web)
- Timeframe: Emerging concept (currently in development)
- Gavin Wood, founder of Ethereum, used the term Web3 first in 2014.
- Nature: Intelligent, decentralized, user-centric
- Features:
- Semantic web: Web 3.0 aims to make the web more intelligent and capable of understanding and processing information in a way that mimics human cognition (i.e., machine-readable data).
- Personalization and AI: Web 3.0 leverages artificial intelligence (AI), machine learning (ML), and natural language processing (NLP) to create more personalized and intuitive user experiences. Websites and apps will be able to predict user needs and provide tailored information.
- Decentralization: One of the major components of Web 3.0 is a shift toward decentralization, using technologies like blockchain to give users more control over their data and interactions online.
- Smart contracts and blockchain: These technologies enable secure, decentralized transactions without the need for central authorities (such as banks or other intermediaries).
- Interoperability: Web 3.0 will allow seamless interactions across platforms, devices, and applications, enabling a more connected experience.
- Virtual and augmented reality (VR/AR): The web will increasingly incorporate immersive experiences through VR and AR technologies, creating a more interactive and engaging user experience.
- 3D Web: The evolution towards a 3D web involves web environments where users can interact in virtual spaces, playing games, working, and socializing in an immersive manner.
- Example:
- Decentralized applications (dApps) running on blockchain platforms (e.g., Ethereum)
- Virtual worlds like those in the metaverse
- AI-powered web assistants (like Siri, Alexa, etc.)
Web 1.0 focused on delivering information, Web 2.0 made the web more interactive and social, and Web 3.0 is transforming the web into an intelligent, decentralized, and user-centric ecosystem.
| Aspect | Web 1.0 | Web 2.0 | Web 3.0 |
| User Interaction | Read-only, passive consumption | Active participation, user-generated content | Collaborative, intelligent interaction, personalized |
| Content Creation | Limited to website owners and developers | Users generate and share content (social media, blogs) | Decentralized content creation, AI-generated content |
| Technologies | HTML, basic CSS, static content | JavaScript, AJAX, APIs, dynamic content | AI, Machine Learning, Blockchain, Smart Contracts, VR/AR |
| Type of Web Pages | Static, fixed pages | Dynamic, user-interactive pages | Adaptive, AI-powered, semantic, immersive |
| Monetization | Limited to ads on static sites | Ad-driven, freemium models, social media influencers | Tokenization, cryptocurrency, decentralized finance (DeFi) |
| Data Ownership | Centralized control by website owners | User-generated content but still centralized | Decentralized, users have control over their data |
| Privacy and Security | Basic security, passwords, limited encryption | Improved encryption, social security concerns | Strong encryption, blockchain for secure transactions, more privacy control for users |
| Interactivity Level | Minimal (links, text, images) | High (social networks, comments, media sharing) | Very high (AI assistants, smart interactions, decentralized apps) |
| Search and Retrieval | Manual, keywords-based | Enhanced with search engines, recommendation systems | Personalized search, AI-based recommendations, semantic search |
| Content Access | Manual entry of URLs | Accessible through search engines, social links | Accessible through AI-powered assistants, smart agents |
| Communication | Email, basic forms | Social media, real-time chat, video calls | Decentralized communication (peer-to-peer, blockchain-based messaging) |
| Focus | Information sharing | User interaction, collaboration, and content sharing | Smart, personalized experiences, decentralization |
FAQ (Previous year questions)
Aspect
MAC Address
IP Address
Definition
Physical identity of a network device, which is determined by the Network Interface Card (NIC).
Logical address of signals, used to identify and communicate with a device within the network.
Assigned By
Manufacturer during hardware production
Internet Service Provider (ISP) or DHCP server
Permanence
Permanent and unique
Dynamic or static (can be reassigned)
Changeability
Cannot be changed
Can be changed when switching networks
Routing Role
Operates at Data Link Layer (Layer 2)
Operates at Network Layer (Layer 3)
